cokeBeer
cokeBeer
这里输入com.ss.andriod.ugc.trill直接报错了。 如果输入TikTok可以attach,但是后面inject dex又会失败 
## 本 poc 是检测什么漏洞的 Jetty Ambiguous Paths Information Disclosure Vulnerability (CVE-2021-34429) ## 测试环境 https://github.com/vulhub/vulhub/tree/master/jetty/CVE-2021-34429 ## 备注
### Gogs version v0.12.9 ### Git version - Server: 2.24.1 - Client: 2.24.1 ### Operating system MacOS 10.15.4 ### Database SQLite3 ### Describe the bug in changelog of 0.12.9, https://github.com/gogs/gogs/issues/6901...
报错如下图 
## 改动内容 添加了一个绕过JEP290的RMIConnect类型的payload。 ## 改动原因 目前ysomap内置的RMIConnect类型的payload都是依靠RemoteObject.readObject来触发UnicastRef的readExternal方法。在RMIRegistryExploit中使用Naming.lookup方法发送RemoteObject及其子类的对象。 这里我添加了一个直接返回UnicastRef对象的payload,然后在RMIRegistryExploit中使用更加底层的RemoteCall.invoke来发送UnicastRef类型的对象。远端反序列化UnicastRef,触发反连。 ## 适用场景 适用场景为过滤了RemoteObejct但是未过滤UnicastRef的场合。现实的例子可见于Weblogic T3反序列化漏洞的绕过。 ## 实际测试 测试图片中返回了远端的类型异常,但是反连已经发生了
**Describe the bug** I tried all codes in https://docs.spring.io/spring-security/reference/servlet/authorization/authorize-http-requests.html, but they all failed to work **To Reproduce** configure codes in a SecurityConfig.java file in my springboot, which is migrated from...
**What steps does it take to reproduce the issue?** post ddi to import dataverse like ``` POST /api/batch/import?key={your_key} Host: demo.dataverse.org Cookie: {your_cookie} Content-Type: application/xml Content-Length: 4127 OTC Stock Historical Datadoi:10.70122/FK2/YE2UKMDemo...
**Describe the bug** Run [bady_fuzzer.py](https://github.com/AFLplusplus/LibAFL/blob/main/fuzzers/baby_fuzzer/baby_fuzzer.py), fuzz end but no crash file generated. **To Reproduce** Steps to reproduce the behavior: 1. run bady_fuzzer.py **Expected behavior** Crash file generated **Screen output/Screenshots** 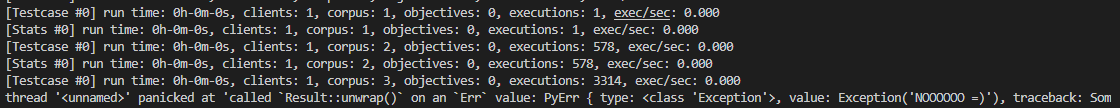...
Hello 👋 I found a potential security issue in Kuboard-spray, how can I get in touch with you in a private way and submit my security report? Could you add...
