LuckyC4t
Results
1
issues of
LuckyC4t
in `framework/phpok_call.php`, the function `_userlist` has a sql injection  in some reasons, we can controll the value of variable `$rs`, so we can splice evil sql query  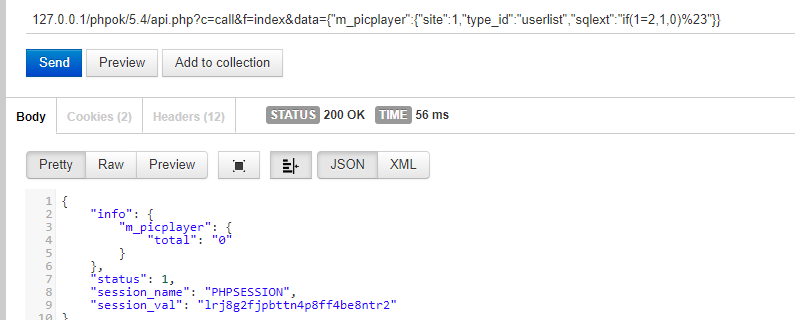...
