The functionality add attachment to parts allows access to local files.
Bug description
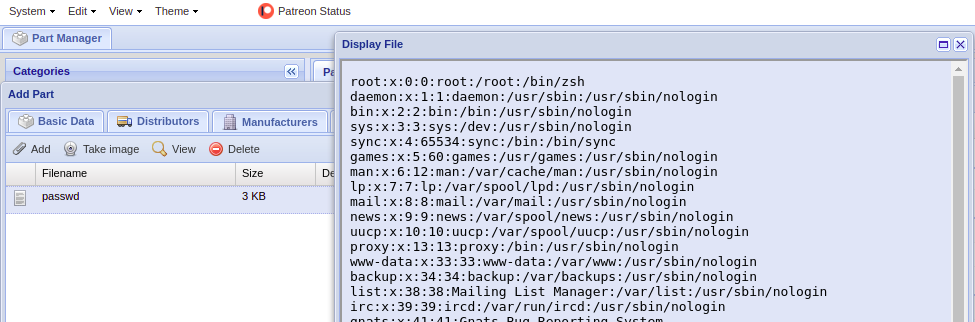
In PartKeepr before v1.4.0, the functionality to load attachments using a URL when creating a part, allows the use of the file:// URI scheme, allowing local files to be read.
Steps to reproduce
- Go to 'Add Part'.
- Click on 'Attachments'.
- Click on 'Add'.
- Fill the 'URL' field with "file:///etc/passwd".
- Click on the uploaded file in order to see the content.
Expected behavior
The application should not allow access to local files.
Observed behavior
Local paths can be used to read files on the system.
Screenshots and files

System Information
- PartKeepr Version: v1.4.0 and v0.1.9
- Operating System: Linux
- Web Server: Apache
- PHP Version: 7.4
- Database and version: Mysql
- Reproducible on the demo system: Yes.
This is how most users add locally stored / downloaded data sheets / images etc. Does this allow access to resources that the user does not have permissions for?
On 4 Jan 2022, at 13:53, alestorm980 @.***> wrote:
Bug description
In PartKeepr before v1.4.0, the functionality to load attachments using a URL when creating a part, allows the use of the file:// URI scheme, allowing local files to be read.
Steps to reproduce
Go to 'Add Part'. Click on 'Attachments'. Click on 'Add'. Fill the 'URL' field with "file:///etc/passwd". Click on the uploaded file in order to see the content. Expected behavior
The application should not allow access to local files.
Observed behavior
Local paths can be used to read files on the system.
Screenshots and files
System Information
PartKeepr Version: v1.4.0 and v0.1.9 Operating System: Linux Web Server: Apache PHP Version: 7.4 Database and version: Mysql Reproducible on the demo system: Yes. — Reply to this email directly, view it on GitHub, or unsubscribe. You are receiving this because you are subscribed to this thread.
Yes, it is possible to read files within the server to which the user running the application has access, this includes source code, system configuration files, ssh keys, etc.
For example here an attacker can read a ssh key from the user running the application.

I attach the link to the advisory https://fluidattacks.com/advisories/hendrix/