Rework Roles and Policies
This is an umbrella issue to track all the changes to Roles and Policies. The following diagram shows the entities related to access control functionality.
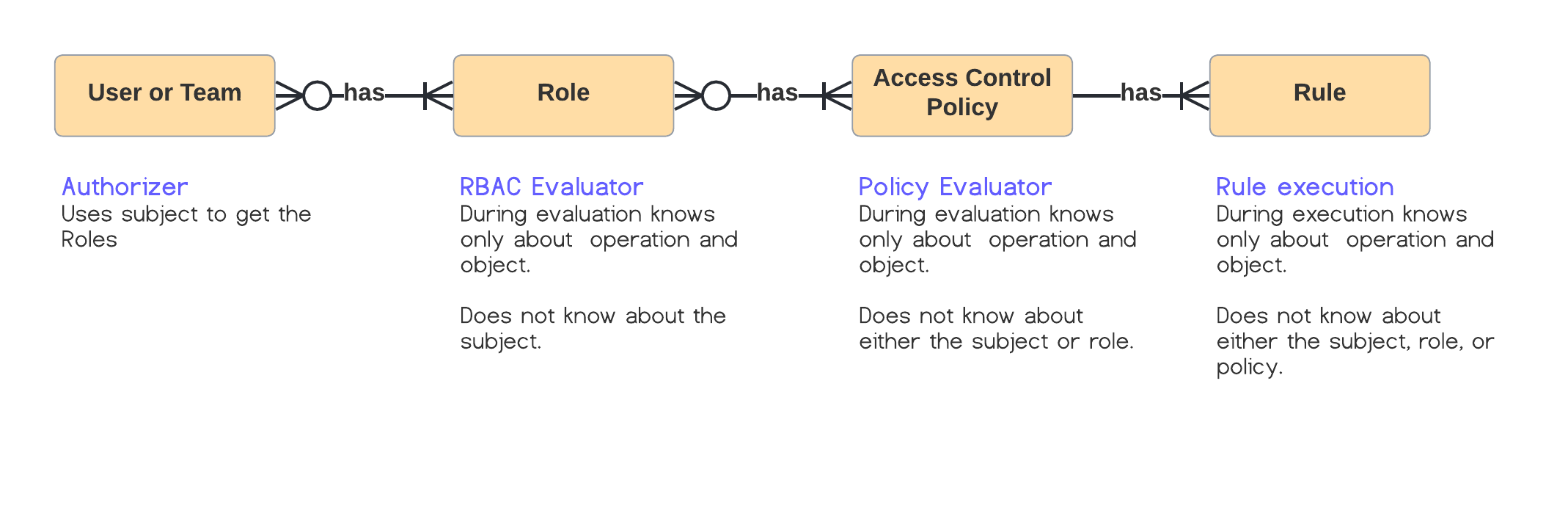
Roles and Policies for Access Control are described in this blog. Few changes are being made from the previous version.
API and Modeling changes:
- A
Rolenow has one or morePolicieswith a 1:N relationship instead of a 1:1 relationship.CreateRolenow requires at least one policy to be attached to a role. A policy is not automatically created during the creation of a role. - Policies that the system comes with have been renamed.
DataConsumerAccessControlPolicyis nowDataConsumerPolicyandDataStewardAccessControlPolicyis justDataStewardPolicy. - A policy has rules. Both the policy and the rule had an
enabledflag. Now theenabledflag per rule is removed.
For more details and implementation changes, see the description of the following tasks:
- #3031
- #3776
- #4113
- #4120
- #4166
- #4170
- #5509
- #5558
- #2907
- #3032
- #4079
- #4580
- #3553
- #4677
- #6172
- #6336
- #6365
- #6368
- #6391
- #6518
- #6631
- #6676
- #6719
- #6723
- #6728
- #6860
- #6886
- #7072
- #7145
- #7181
- #7643
in 0.11 following tasks will be addressed
- [ ] #4677
- [ ] #4580
- [ ] #4079
- [ ] #3776
- [ ] #3316
- [ ] #3050
- [ ] #3032
- [ ] #2762
- [ ] #4684
- [ ] #5246
- [ ] #4684
- [ ] #5311
Currently, policies capture minimal operations through UI and APIs are enforcing the permissions in a generic way. We are going to enumerate all the operations that are possible through UI or APIs and have admins create policies at Site-wide/Domain/Entity level and Settings at Services / Glossaries / Tags etc..
Metadata Operations at Entity
Common Operations across Entities
- SuggestDescription - Allowed by Default, Ideally grouping actions on Suggest based ones and allowing them by default unless there is an explicitly stated rule to deny
- SuggestTags
- UpdateDescription
- UpdateTags
- UpdateOwner
- UpdateTier
- UpdateCustomFields
- Read PII Tags data
- Write PII Tags data
- Soft Delete Entity
- Hard Delete Entity
- Create/update Lineage
Table
- Read Sample Data
- Write Sample Data
- Create/Update Data Quality Test
- Read Data Quality Tests
- Read Sample Queries
- Create/Update Sample Queries
- Read Profiler data
- Write Profiler data
Topic
- Write sample data to a Topic
- Read sample data on a topic
Dashboards
No additional special permissions for now
Pipelines
No Additional special permissions for now
ML Models
No Additional special permissions for now
Glossaries
- Add Glossary
- Add Glossary Term
- Read -> is default no special permission is needed
- Assign Owner
- Assign Reviewer
- Delete Glossary
Tags & Tag Category
- Add a Tag Category
- Add a Tag
- Read -> Default allow
- Delete Tag
- Delete Tag Category
Services - Default Admin only
- Add a Service
- Read Service connection details
- Add Ingestion
Webhooks - Admin only
Teams & Users
- Add a user
- Delete a User
- Add a Team
- Assign Team owner
- Team Owner should be able to add/remove users and perform other ops such as adding the description
Add Bot - Admin only
- Domain level policy restrictions, A policy should have an option to evaluate the site-wide or at the domain level.
- Admin while creating a policy should be able to input a domain into the policy and at the evaluation, the authorizer should accept the Entity domain it's validating against and the user's policy details and see if the user policy states that they can access the domain's entities and which operations they are allowed to perform. If the User doesn't have the domain in the policy they shouldn't be able to access any entities if they do have the domain access we will evaluate the operations similar to site-wide access but within that domain
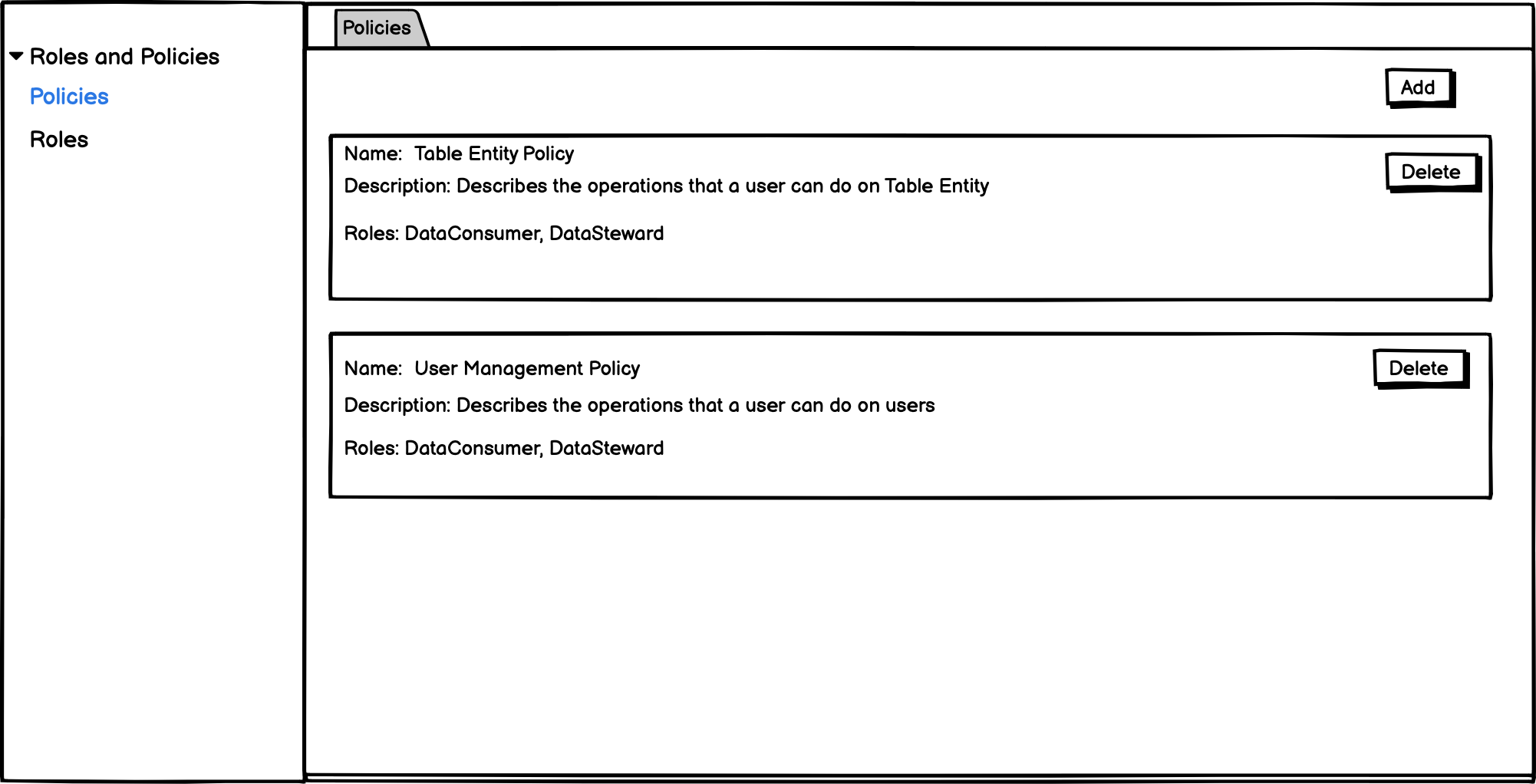

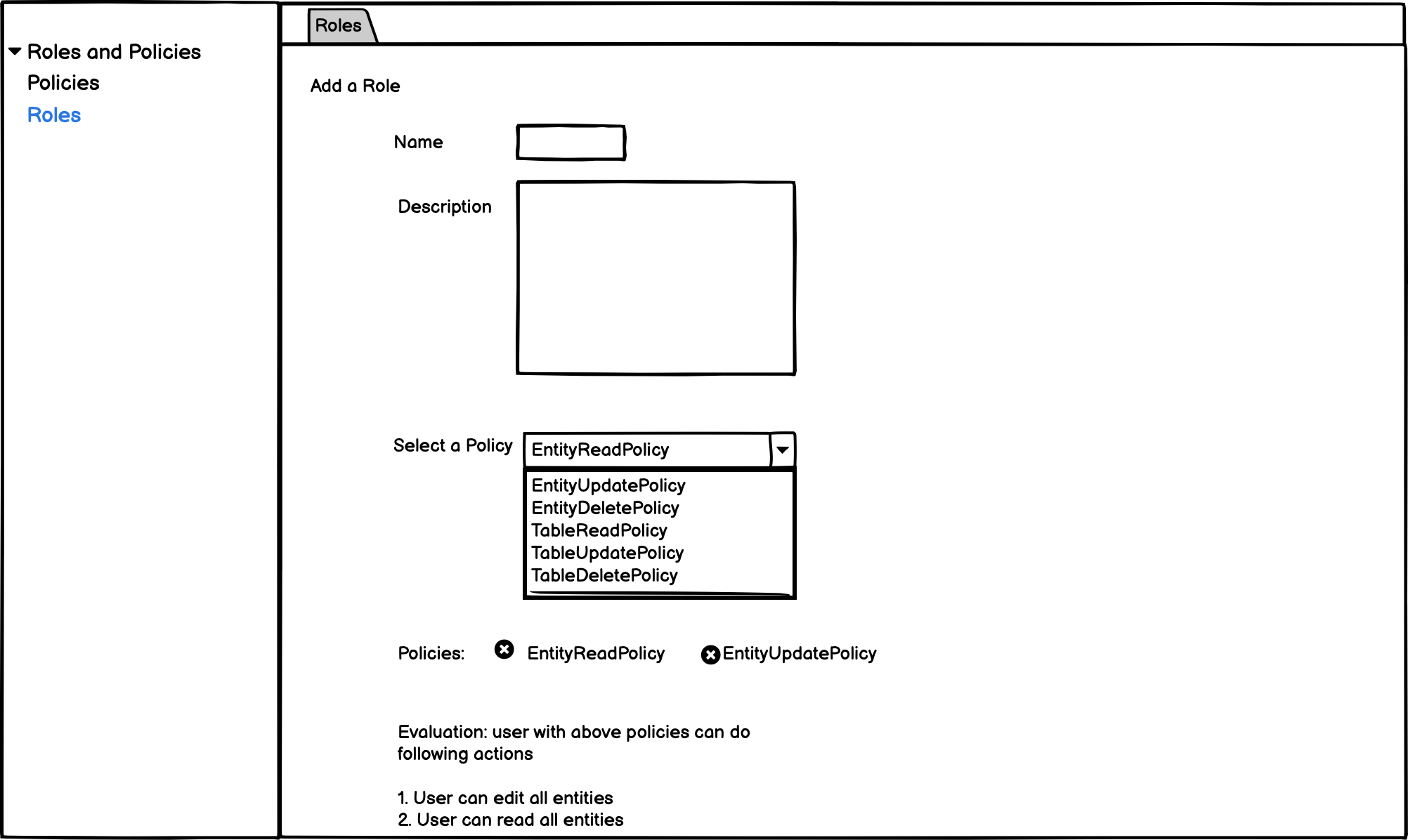
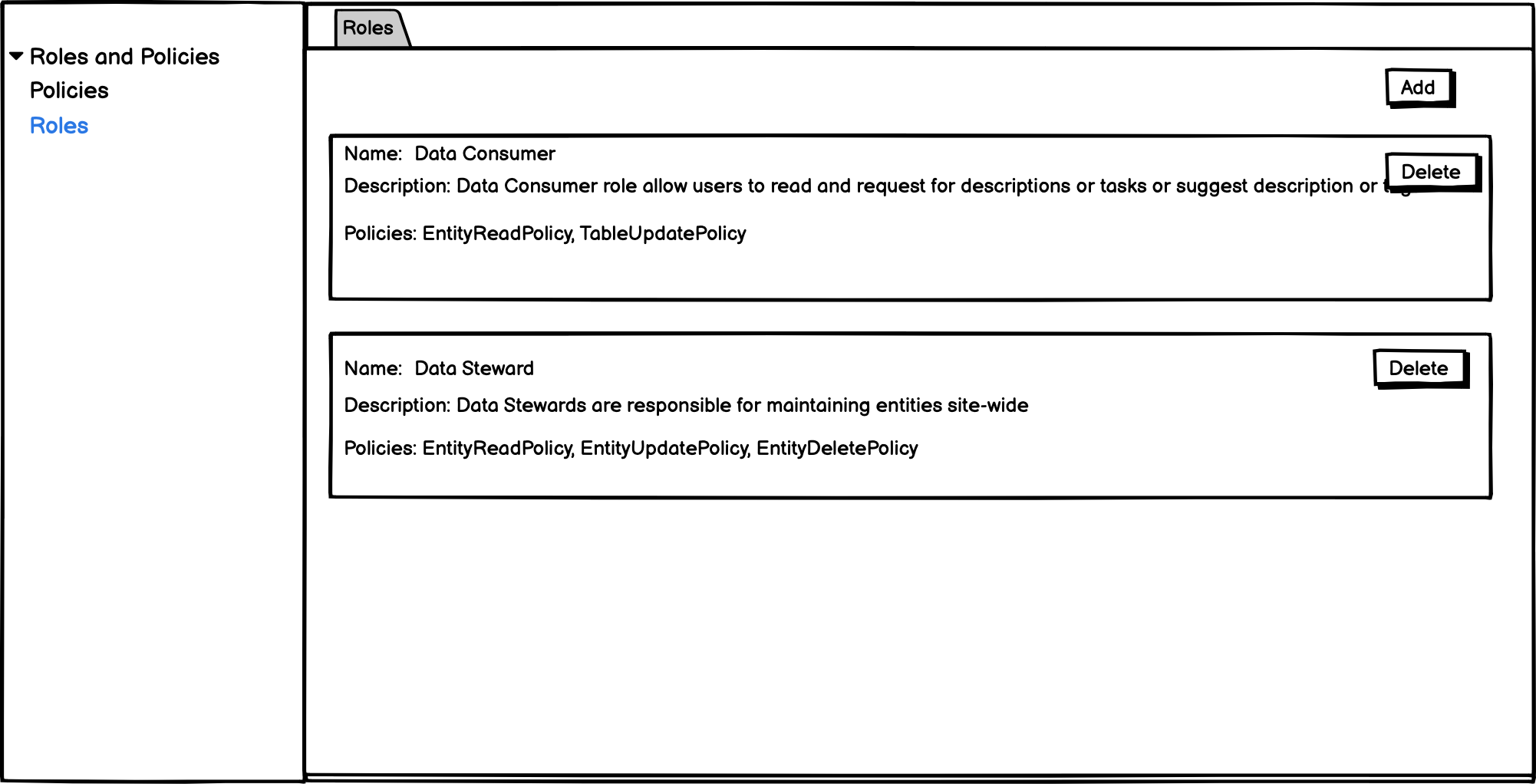
- We need to build APIs for a role with multiple policies to retrieve the allowed operations by going through all the policies. That will help summarize what operations an admin is giving to a policy while creating
- Another API for a logged In user, based on the roles they got assigned to what policies they have, and finally what operations they can perform. UI can make this request to see what tabs they need to show and if they should make an API call such as a sample data call should they make this one or not and also hide components such as edit description if they do not have edit description or suggest description option