HFish
 HFish copied to clipboard
HFish copied to clipboard
安全、可靠、简单、免费的企业级蜜罐
我利用服务器搭建了蜜罐管理和节点,也成功部署了高交互蜜罐,但攻击者尝试登录后,返回的是连接被拒绝。我参照文档中的测试账号和密码尝试连接高交互ssh蜜罐,也是返回Connection closed by foreign host. 根据文档的描述,需要与zoo.hfish.net连通,但这个地址貌似已经失效了,无法ping通,这将要如何操作。我希望通过高交互蜜罐进一步分析攻击者的行为及其上传的恶意文件,请问该如何解决。
版本:3.0.1 在大屏中看到的“近期攻击事件”的源IP非真实的客户端IP,为我自己的出口公网ip,我蜜罐放在互联网上,IP是做了dnat转换的才能访问我的蜜罐的,请教下这个要如何修改配置。
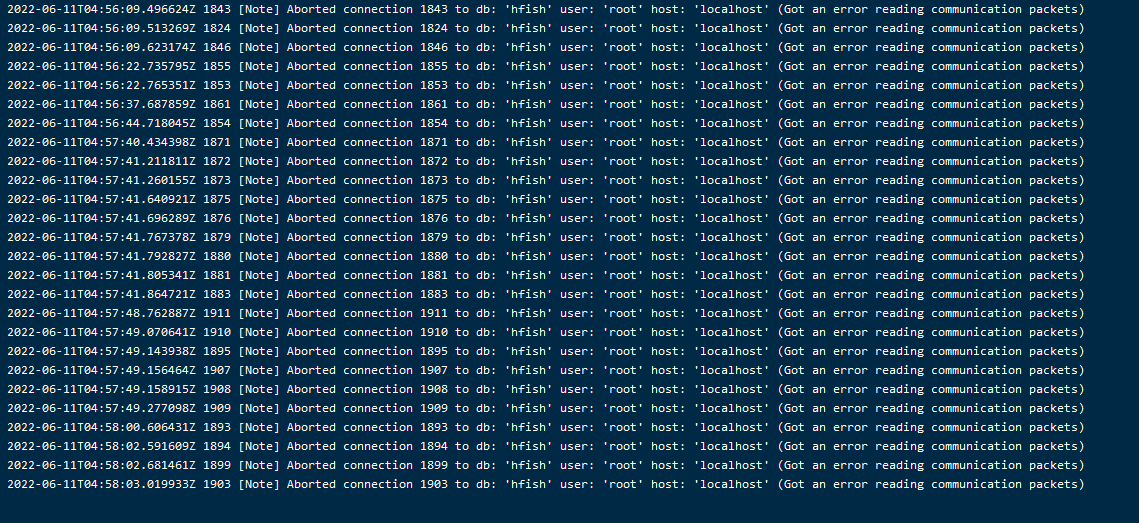  ``` 2022-06-10 21:52:43.272 [ERRO] clients.go:83: insert host[pF3oVk7lcd3jnH0kfzgKAwIL] err: context canceled, INSERT INTO `hosts`(`disk_total`,`dns_info`,`host_id`,`os_arch`,`mem_used`,`time_zone`,`cpu_num`,`mem_total`,`disk_used`,`net_info`,`client_id`,`platform`) VALUES(0,'','','',0,'',0,0,0,'','pF3oVk7lcd3jnH0kfzgKAwIL','') Stack: 1. hfish/internal/server/handler.AddClient /usr/local/share/internal/server/handler/clients.go:83 2. github.com/gin-gonic/gin.(*Context).Next /root/go/pkg/mod/github.com/gin-gonic/[email protected]/context.go:168 3. hfish/internal/server/router.TlsHandler.func1 /usr/local/share/internal/server/router/router.go:42 4. github.com/gin-gonic/gin.(*Context).Next /root/go/pkg/mod/github.com/gin-gonic/[email protected]/context.go:168 5....
root@ubuntu:~# ./client 2022/06/10 05:29:39 log dir: /root/logs 2022-06-10 05:29:39.769 [INFO] client.go:58: client work path: /root 2022-06-10 05:29:39.777 [WARN] service.go:170: fetch client id fail: 节点数已超出限制,不能新增 2022-06-10 05:29:39.778 [WARN] service.go:189: fetch client...
~ sudo docker logs hfish standard_init_linux.go:228: exec user process caused: exec format error https://www.lewuathe.com/exec-format-error-in-docker-container.html 应该是启动脚本需要更新一下,谢谢回复。
配置文档里面没看到HTTPS证书配置相关文档
this can allow a high -performance MASTER bowl of non -public network. Through FRP, Rathole and other internal network penetration tools, connecting multiple 1 core 512M and other public network...
使用防火墙进行蜜罐联动,动态流量转发时攻击IP显示异常,显示的都是防火墙的IP
