authentik

authentik copied to clipboard
Proxy with etherpad stuck in "Loading" screen.
Describe your question/ Trying to configure proxy authentication for etherpad, but it gets stuck in loading.
Relevant infos
- Authentik at https://authentik.example.com, internal is https://authentik.localdomain:9443
- Etherpad at https://etherpad.example.com, internal is http://etherpad.localdomain:80
- HAProxy as the reverse proxy. https://etherpad.example.com points to https://authentic.localdomain:9443
- Using embedded outpost
- SAML provider with Grist is working fine, so Authentik seems to be otherwise functional
- Getting a 400 error in the redirect URL on the screen stuck on "Loading..."
- URL: https://etherpad.example.com/outpost.goauthentik.io/callback?X-authentik-auth-callback=true&code=long-hex-value&state=long-hex-value
- curl on https://etherpad.example.com/outpost.goauthentik.io/ping returns
HTTP/2 204
Screenshots
Stuck in "Loading" screenshot

Outpost seems to be ok
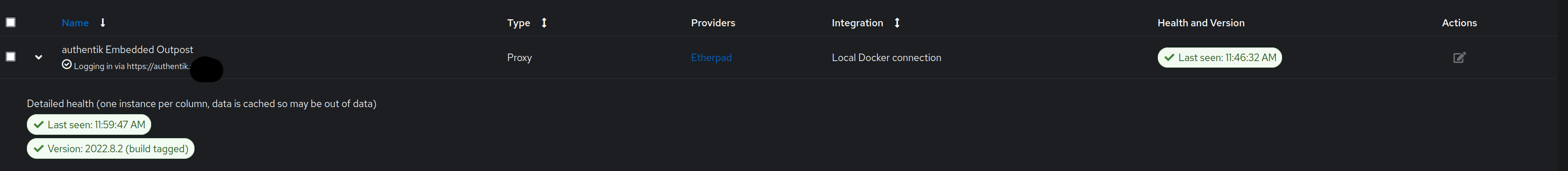
Provider config

Application config

Logs
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"app":"Etherpad","event":"Found app based direct host match","host":"etherpad.example.com","level":"trace","logger":"authentik.outpost.proxyv2","timestamp":"2022-09-16T10:38:45-07:00"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"event":"passing to application mux","host":"etherpad.example.com","level":"trace","logger":"authentik.outpost.proxyv2","timestamp":"2022-09-16T10:38:45-07:00"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"event":"handling OAuth Callback from querystring signature","level":"debug","logger":"authentik.outpost.proxyv2.application","name":"Etherpad","timestamp":"2022-09-16T10:38:45-07:00"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"event":"hello'd","level":"trace","logger":"authentik.outpost.ak-api-controller","loop":"ws-health","timestamp":"2022-09-16T10:38:45-07:00"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"auth_via": "unauthenticated", "event": "Code is expired", "host": "localhost:8000", "level": "warning", "logger": "authentik.providers.oauth2.views.token", "pid": 25, "request_id": "b7294880df3b49a1bc0d248278c86c5c", "timestamp": "2022-09-16T17:38:45.963655", "token": "8a8cfbc43235434c8ff8ef28410ca00b"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"auth_via": "unauthenticated", "event": "/application/o/token/", "host": "localhost:8000", "level": "info", "logger": "authentik.asgi", "method": "POST", "pid": 25, "remote": "127.0.0.1", "request_id": "b7294880df3b49a1bc0d248278c86c5c", "runtime": 58, "scheme": "http", "status": 400, "timestamp": "2022-09-16T17:38:45.969495", "user": "", "user_agent": "goauthentik.io/outpost/2022.8.2 (provider=Etherpad)"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"event": "Bad Request: /application/o/token/", "level": "warning", "logger": "django.request", "timestamp": 1663349925.9715006}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"error":"oauth2: cannot fetch token: 400 Bad Request\nResponse: {\"error\": \"invalid_grant\", \"error_description\": \"The provided authorization grant or refresh token is invalid, expired, revoked, does not match the redirection URI used in the authorization request, or was issued to another client\"}","event":"failed to redeem code","level":"warning","logger":"authentik.outpost.proxyv2.application","name":"Etherpad","timestamp":"2022-09-16T10:38:45-07:00"}
Sep 16 10:38:45 darkstar docker-authentik-server-start[3451059]: {"event":"/outpost.goauthentik.io/callback?X-authentik-auth-callback=true&code=8a8cfbc43235434c8ff8ef28410ca00b&state=mM7Szp7VjqWde_VzdRHc0zy7KOmCZcoS4CrH5LGh_c0","host":"etherpad.example.com","level":"info","logger":"authentik.outpost.proxyv2.application","method":"GET","name":"Etherpad","remote":"10.0.0.91","runtime":"70.636","scheme":"","size":0,"status":400,"timestamp":"2022-09-16T10:38:45-07:00","upstream":"","user_agent":"Mozilla/5.0 (X11; Linux x86_64; rv:104.0) Gecko/20100101 Firefox/104.0"}
Sep 16 10:38:46 darkstar docker-authentik-server-start[3451059]: {"event":"tracing request to backend","headers":{"Accept":["*/*"],"Accept-Encoding":["gzip, deflate, br"],"Accept-Language":["en-US,en;q=0.5"],"Cache-Control":["no-cache"],"Connection":["Upgrade"],"Cookie":["authentik_csrf=GHXSygWfDdv4hJDsfGjeVbieHpRhk00I; authentik_session=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzaWQiOiIxNWdoeGo4cjN6MHR6NWN4Y3QxNWp1OXhmd2g0Nmk5cSIsImlzcyI6ImF1dGhlbnRpayIsInN1YiI6ImFkNTRjYmVlZTZhZmEzZTRiZTRlMmYxNDIxZDNlOTFjNTc1MDhiOTM2MDkzNjNmMGZhNzhkZjFhNjQ3MDY1NmIiLCJhdXRoZW50aWNhdGVkIjp0cnVlLCJhY3IiOiJnb2F1dGhlbnRpay5pby9jb3JlL2RlZmF1bHQifQ.KEMXhm1HZral_5IgFq-2pX3fJOCslCndEhybrMkLsTA"],"Dnt":["1"],"Origin":["https://authentik.example.com"],"Pragma":["no-cache"],"Sec-Fetch-Dest":["websocket"],"Sec-Fetch-Mode":["websocket"],"Sec-Fetch-Site":["same-origin"],"Sec-Websocket-Extensions":["permessage-deflate"],"Sec-Websocket-Key":["Cqd/RiJhN4gef1nQ9aLInQ=="],"Sec-Websocket-Version":["13"],"Upgrade":["websocket"],"User-Agent":["Mozilla/5.0 (X11; Linux x86_64; rv:104.0) Gecko/20100101 Firefox/104.0"],"X-Forwarded-For":["10.0.0.91"],"X-Forwarded-Proto":["https"]},"level":"trace","logger":"authentik.router","timestamp":"2022-09-16T10:38:46-07:00","url":"http://localhost:8000/ws/client/"}
Sep 16 10:38:46 darkstar docker-authentik-server-start[3451059]: {"event":"tracing request to backend","headers":{"Accept":["*/*"],"Accept-Encoding":["gzip, deflate, br"],"Accept-Language":["en-US,en;q=0.5"],"Cache-Control":["no-cache"],"Connection":["Upgrade"],"Cookie":["authentik_csrf=GHXSygWfDdv4hJDsfGjeVbieHpRhk00I; authentik_session=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzaWQiOiIxNWdoeGo4cjN6MHR6NWN4Y3QxNWp1OXhmd2g0Nmk5cSIsImlzcyI6ImF1dGhlbnRpayIsInN1YiI6ImFkNTRjYmVlZTZhZmEzZTRiZTRlMmYxNDIxZDNlOTFjNTc1MDhiOTM2MDkzNjNmMGZhNzhkZjFhNjQ3MDY1NmIiLCJhdXRoZW50aWNhdGVkIjp0cnVlLCJhY3IiOiJnb2F1dGhlbnRpay5pby9jb3JlL2RlZmF1bHQifQ.KEMXhm1HZral_5IgFq-2pX3fJOCslCndEhybrMkLsTA"],"Dnt":["1"],"Origin":["https://authentik.example.com"],"Pragma":["no-cache"],"Sec-Fetch-Dest":["websocket"],"Sec-Fetch-Mode":["websocket"],"Sec-Fetch-Site":["same-origin"],"Sec-Websocket-Extensions":["permessage-deflate"],"Sec-Websocket-Key":["y2xnubStp9BEnwd/O0TwjQ=="],"Sec-Websocket-Version":["13"],"Upgrade":["websocket"],"User-Agent":["Mozilla/5.0 (X11; Linux x86_64; rv:104.0) Gecko/20100101 Firefox/104.0"],"X-Forwarded-For":["10.0.0.91"],"X-Forwarded-Proto":["https"]},"level":"trace","logger":"authentik.router","timestamp":"2022-09-16T10:38:46-07:00","url":"http://localhost:8000/ws/client/"}
Sep 16 10:38:46 darkstar docker-authentik-server-start[3451059]: {"event":"tracing request to backend","headers":{"Accept":["*/*"],"Accept-Encoding":["gzip, deflate, br"],"Accept-Language":["en-US,en;q=0.5"],"Cache-Control":["no-cache"],"Connection":["Upgrade"],"Cookie":["authentik_csrf=GHXSygWfDdv4hJDsfGjeVbieHpRhk00I; authentik_session=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzaWQiOiIxNWdoeGo4cjN6MHR6NWN4Y3QxNWp1OXhmd2g0Nmk5cSIsImlzcyI6ImF1dGhlbnRpayIsInN1YiI6ImFkNTRjYmVlZTZhZmEzZTRiZTRlMmYxNDIxZDNlOTFjNTc1MDhiOTM2MDkzNjNmMGZhNzhkZjFhNjQ3MDY1NmIiLCJhdXRoZW50aWNhdGVkIjp0cnVlLCJhY3IiOiJnb2F1dGhlbnRpay5pby9jb3JlL2RlZmF1bHQifQ.KEMXhm1HZral_5IgFq-2pX3fJOCslCndEhybrMkLsTA"],"Dnt":["1"],"Origin":["https://authentik.example.com"],"Pragma":["no-cache"],"Sec-Fetch-Dest":["websocket"],"Sec-Fetch-Mode":["websocket"],"Sec-Fetch-Site":["same-origin"],"Sec-Websocket-Extensions":["permessage-deflate"],"Sec-Websocket-Key":["dx9sKmDY8CC2dyoJ1UoKwQ=="],"Sec-Websocket-Version":["13"],"Upgrade":["websocket"],"User-Agent":["Mozilla/5.0 (X11; Linux x86_64; rv:104.0) Gecko/20100101 Firefox/104.0"],"X-Forwarded-For":["10.0.0.91"],"X-Forwarded-Proto":["https"]},"level":"trace","logger":"authentik.router","timestamp":"2022-09-16T10:38:46-07:00","url":"http://localhost:8000/ws/client/"}
Sep 16 10:38:50 darkstar docker-authentik-server-start[3451059]: {"event":"tracing request to backend","headers":{"Accept":["*/*"],"User-Agent":["goauthentik.io lifecycle Healthcheck"]},"level":"trace","logger":"authentik.router","timestamp":"2022-09-16T10:38:50-07:00","url":"http://localhost:8000/-/health/ready/"}
Sep 16 10:38:50 darkstar docker-authentik-server-start[3451059]: {"auth_via": "unauthenticated", "event": "/-/health/ready/", "host": "localhost:9000", "level": "info", "logger": "authentik.asgi", "method": "HEAD", "pid": 26, "remote": "127.0.0.1", "request_id": "016beb0b3a5a46739110c9e1cd580d74", "runtime": 20, "scheme": "http", "status": 204, "timestamp": "2022-09-16T17:38:50.034599", "user": "", "user_agent": "goauthentik.io lifecycle Healthcheck"}
Sep 16 10:38:55 darkstar docker-authentik-server-start[3451059]: {"event":"hello'd","level":"trace","logger":"authentik.outpost.ak-api-controller","loop":"ws-health","timestamp":"2022-09-16T10:38:55-07:00"}
Sep 16 10:38:59 darkstar docker-authentik-server-start[3451059]: {"auth_via": "unauthenticated", "event": "/-/health/live/", "host": "localhost:8000", "level": "info", "logger": "authentik.asgi", "method": "GET", "pid": 26, "remote": "127.0.0.1", "request_id": "1624628985e4474e86780d4eab08d058", "runtime": 32, "scheme": "http", "status": 204, "timestamp": "2022-09-16T17:38:59.362397", "user": "", "user_agent": "goauthentik.io/proxy/healthcheck"}
Version and Deployment (please complete the following information):
- authentik version: 2022.8.2
- Deployment: NixOS virtualisation.oci-containers.containers (docker)
Additional context
Nix config:
{ config, lib, pkgs, hostParams, userParams, recursiveMerge, ... }:
let
containerDataPath = "/home/${userParams.username}/DockerData";
service_ip = "10.0.0.74";
network = "authentik_network";
in
{
networking.interfaces.${hostParams.mainInterface}.ipv4.addresses = [
{ address = service_ip; prefixLength = 8; }
];
networking.firewall.allowedTCPPorts = [
9000
9443
];
systemd.services = {
"docker-init-network-${network}" = {
description = "Create docker network bridge: ${network}";
after = [ "network.target" ];
wantedBy = [ "multi-user.target" ];
serviceConfig.Type = "oneshot";
script = let cli = "${config.virtualisation.docker.package}/bin/docker";
in ''
if [ "${network}" == "host" ]; then
exit 0
fi
# Put a true at the end to prevent getting non-zero return code, which will
# crash the whole service.
check=$(${cli} network ls | grep "${network}" || true)
if [ -z "$check" ]; then
${cli} network create ${network}
else
echo "container ${network} already exists"
fi
'';
};
};
virtualisation.oci-containers.containers = {
authentik-server = {
image = "ghcr.io/goauthentik/server";
cmd = [ "server" ];
dependsOn = [
"init-network-${network}"
];
extraOptions = [
"--network=${network}"
"--pull=always"
"--env-file=${config.age.secrets.docker.path}"
];
volumes = [
"${containerDataPath}/authentik/media:/media"
"${containerDataPath}/authentik/custom-templates:/templates"
"${containerDataPath}/geoip:/geoip"
];
environment = {
AUTHENTIK_REDIS__HOST = "redis.localdomain";
AUTHENTIK_POSTGRESQL__HOST = "postgres.localdomain";
AUTHENTIK_POSTGRESQL__USER = "nextcloud";
AUTHENTIK_POSTGRESQL__NAME = "authentik";
AUTHENTIK_LOG_LEVEL = "trace";
};
ports = [
"${service_ip}:9000:9000"
"${service_ip}:9443:9443"
];
};
};
virtualisation.oci-containers.containers = {
authentik-worker = {
image = "ghcr.io/goauthentik/server";
cmd = [ "worker" ];
dependsOn = [
"init-network-${network}"
];
extraOptions = [
"--network=${network}"
"--pull=always"
"--env-file=${config.age.secrets.docker.path}"
];
user = "root";
volumes = [
"${containerDataPath}/authentik/media:/media"
"${containerDataPath}/authentik/certs:/certs"
"${containerDataPath}/authentik/custom-templates:/templates"
"${containerDataPath}/geoip:/geoip"
"/var/run/docker.sock:/var/run/docker.sock"
];
environment = {
AUTHENTIK_REDIS__HOST = "redis.localdomain";
AUTHENTIK_POSTGRESQL__HOST = "postgres.localdomain";
AUTHENTIK_POSTGRESQL__USER = "nextcloud";
AUTHENTIK_POSTGRESQL__NAME = "authentik";
};
};
};
};
}