Admins can block pushes that destructively force push with --mirror
Summary
This feature will allow admins to block two potentially dangerous Git commands that are difficult to recover from:
-
git push --mirrorThis is a potentially destructive command for making the remote exactly match the local clone. When run by accident, it can cause many branch deletes and force-pushes at the remote without a warning. -
git push --forcewhenpush.default=matchingPrior to Git v2.0, the commandgit push --forcebehaved likegit push --mirrorbecause of the then-default Git configuration ofpush.default=matching.
Intended Outcome
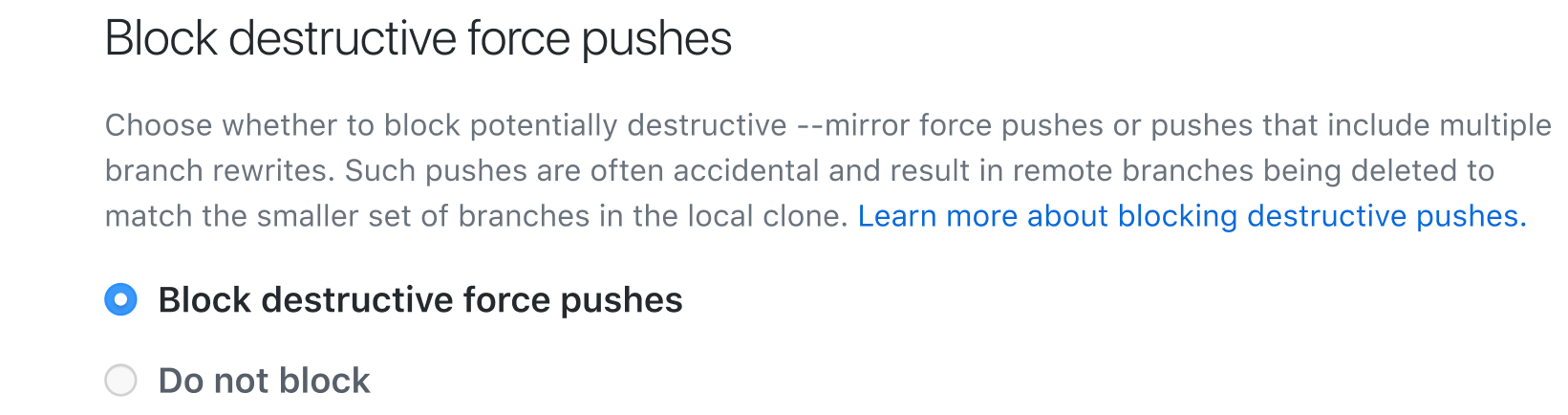
This feature will allow blocking potentially destructive --mirror force pushes or pushes that include multiple branch rewrites.
How will it work?
Admins will be able to enable or disable this feature in repository settings. When enabled, pushes will be rejected when they include multiple branch rewrites and the person who pushed will see an error.
this has shipped to dotcom! 🚢 https://github.blog/changelog/2022-06-15-block-potentially-destructive-git-pushes/
leaving open to track to GHES
🚢 This has shipped with GHES 3.7 release: https://docs.github.com/en/[email protected]/admin/release-notes