Vulnerability processing: False negative for Zoom Desktop app
Links to NVD for 2 vulnerabilities (CVEs) associated with Zoom 5.7.4:
- https://nvd.nist.gov/vuln/detail/CVE-2021-34423
- https://nvd.nist.gov/vuln/detail/CVE-2021-34424
🧑💻 Expected behavior
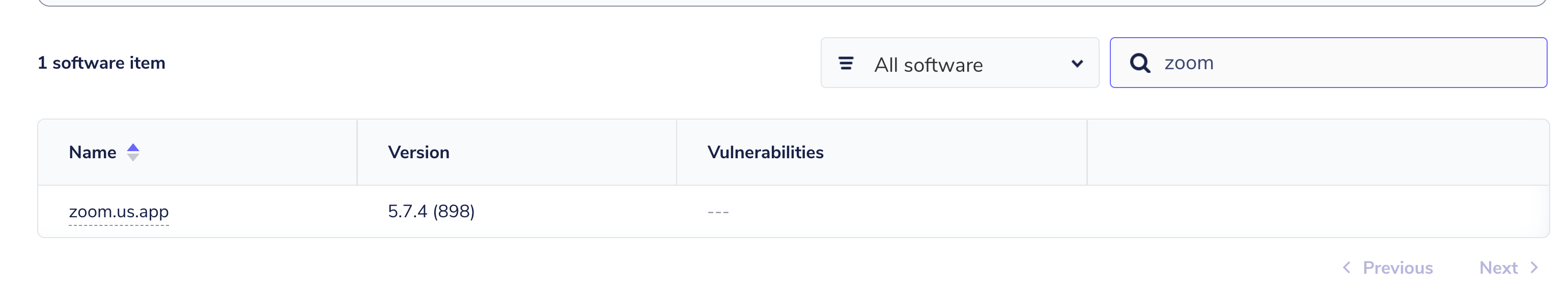
Checking the Zoom version on a laptop, I saw that it was running 5.7.4. I expected to see the above CVEs in Software page in the Fleet UI.
💥 Actual behavior
Here is what I saw:
Notes
- If you go to: https://support.zoom.us/hc/en-us/articles/201361963...
- Find in page 5.8.4
- You will see that CVE-2021-34423 and CVE-2021-34424 were fixed in 5.8.4 in November 2021.
Related
- Parent: https://github.com/fleetdm/fleet/issues/4293
@zhumo @chiiph two things (this only applies to the NVD vuln processing pipeline):
- There's a bug in
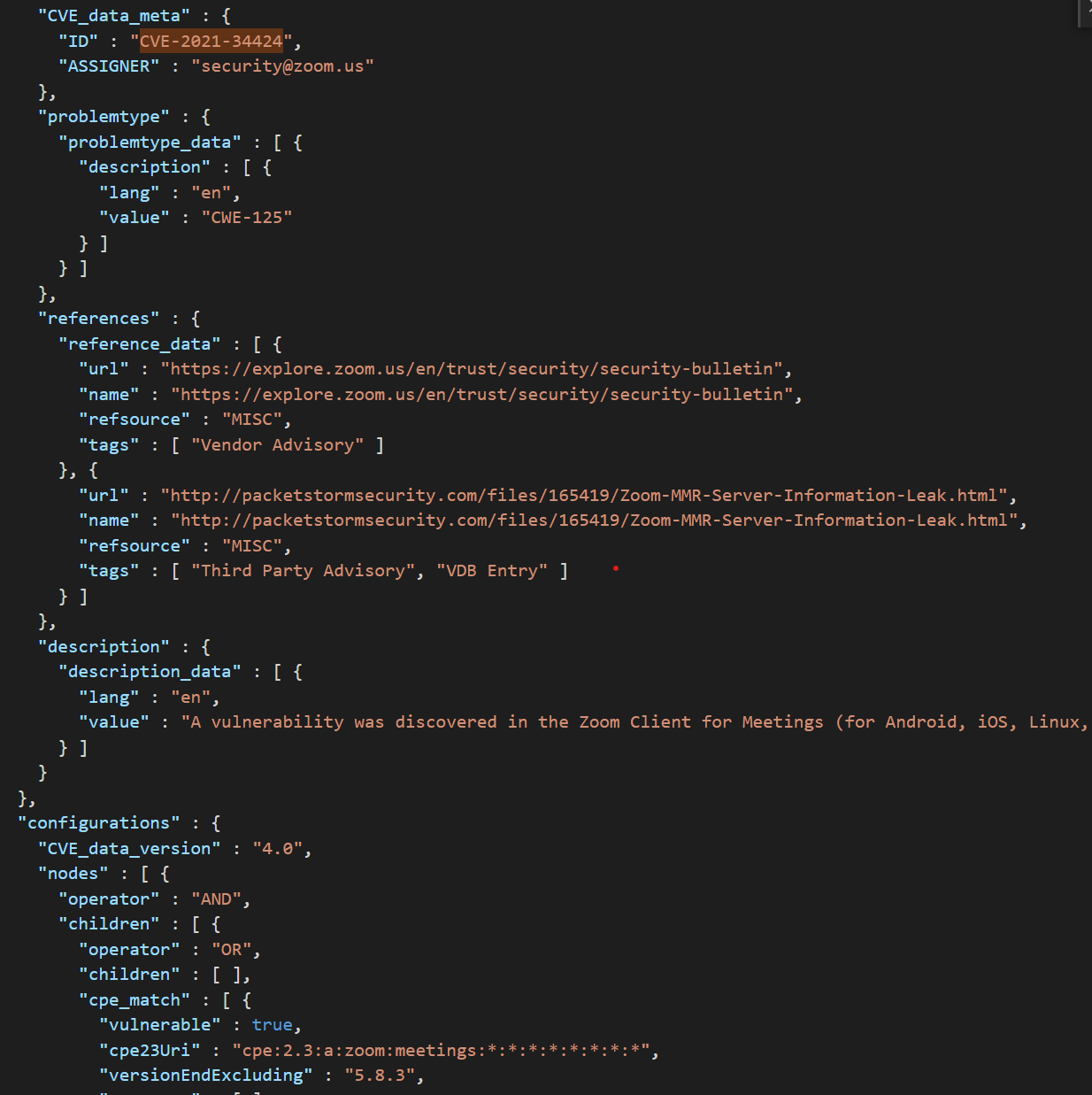
mainwith the way the software version is processed and matched (only tested it on Windows) that is preventing Zoom 5.7.4 to resolve to a CPE (without a CPE there's no way to match CVEs). - Even with the aforementioned bug resolved there's another problem, this is more a limitation with the library we are using for matching CPEs to CVEs. If you look at the entry for CVE-2021-34424 you will see that the matching CPE is
cpe:2.3:a:zoom:meetings:*:*:*:*:*:*:*:*"and then it says"versionEndExcluding" : "5.8.3"- what this basically means is that even though the CPE is specified to match all zoom versions and platforms, the vulnerability only targets versions <=5.8.3, with the library we are currently using, there's no way to check that last part.
So we would need to fork nvdtools and add this functionality? Hrm...
So we would need to fork nvdtools and add this functionality? Hrm...
Probably ... when mapping from CPE to CVE we should be querying for more 'patterns' - currently we only look at exact matches, but if we have a software with the following CPE cpe:2.3:a:zoom:meetings:5.6.1:*:*:*:*:*:windows:* then all the following CPEs should match that cpe:2.3:a:zoom:meetings:*:*:*:*:*:*:windows:*, cpe:2.3:a:zoom:meetings:*:*:*:*:*:*:*:*, cpe:2.3:a:zoom:*:*:*:*:*:*:*:*:*, etc - but without being able to look at the versionEndExcluding property we will have a bunch of false positives.