stack smashing
It is too easy to crash gate with a "stack smashing" error.
For instance, a guest researcher here in our lab uses the alias system to define things like pathnames of input files & output directories and numbers of primaries and then runs lots of jobs with that, using condor. We did our best to avoid that different Gate processes would overwrite each other's files (final output and or intermediate files). Still, typically the first couple of jobs would run successfully, then the rest would crash. The process counter was used in the path of the output directories, so I guessed that maybe with the earlier jobs the file path names would still fit within the buffer, but every time the process counter would cross to a larger power of 10 it would use an extra character, so buffer overflows would start to happen at process number 10, or 100, or 1000, etc.. So I asked her to move/rename her directories such that the path names would be shorter. She did that, and indeed the crashes did not happen anymore.
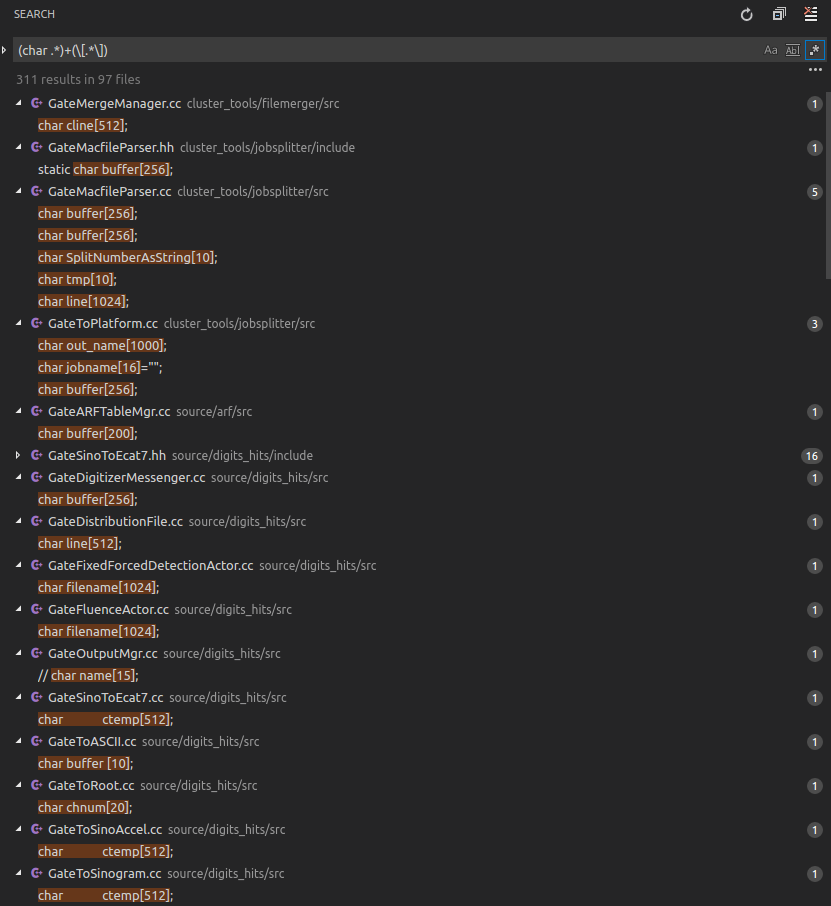
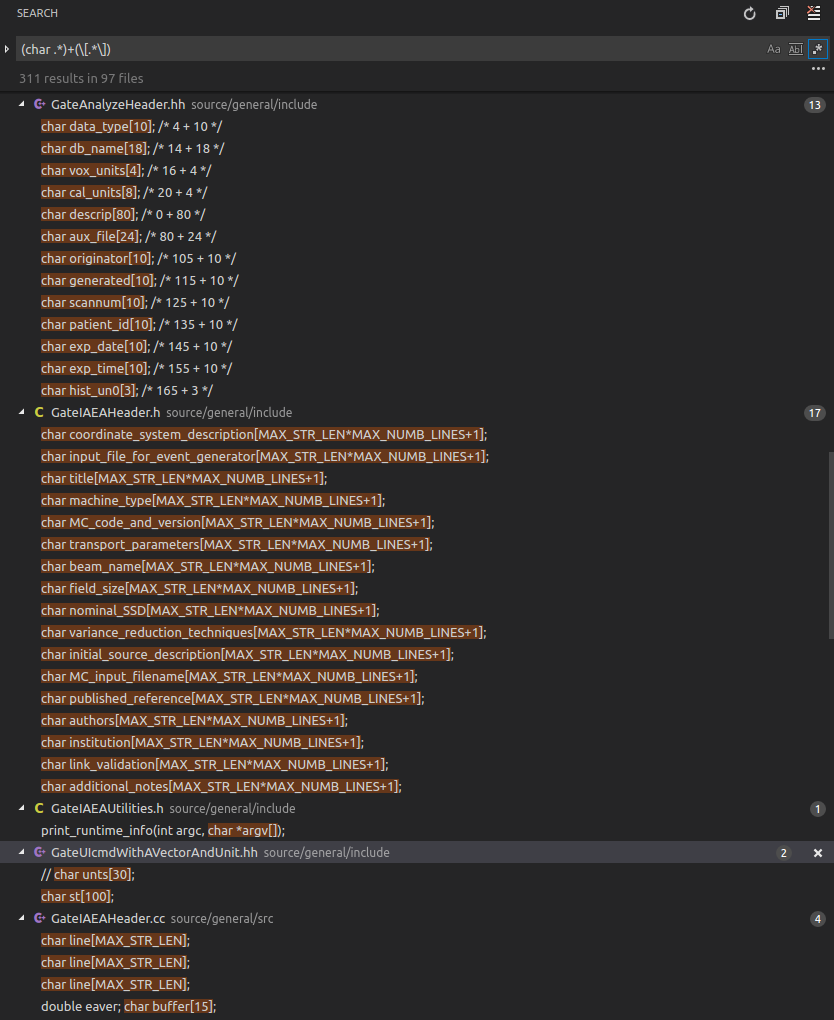
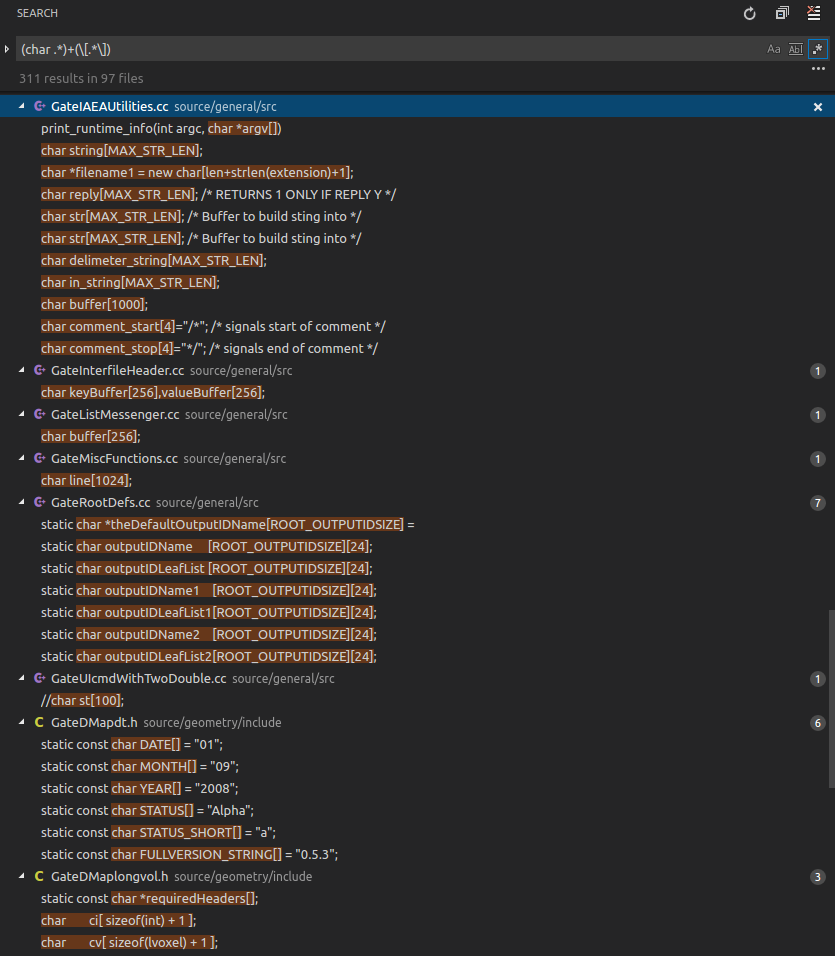
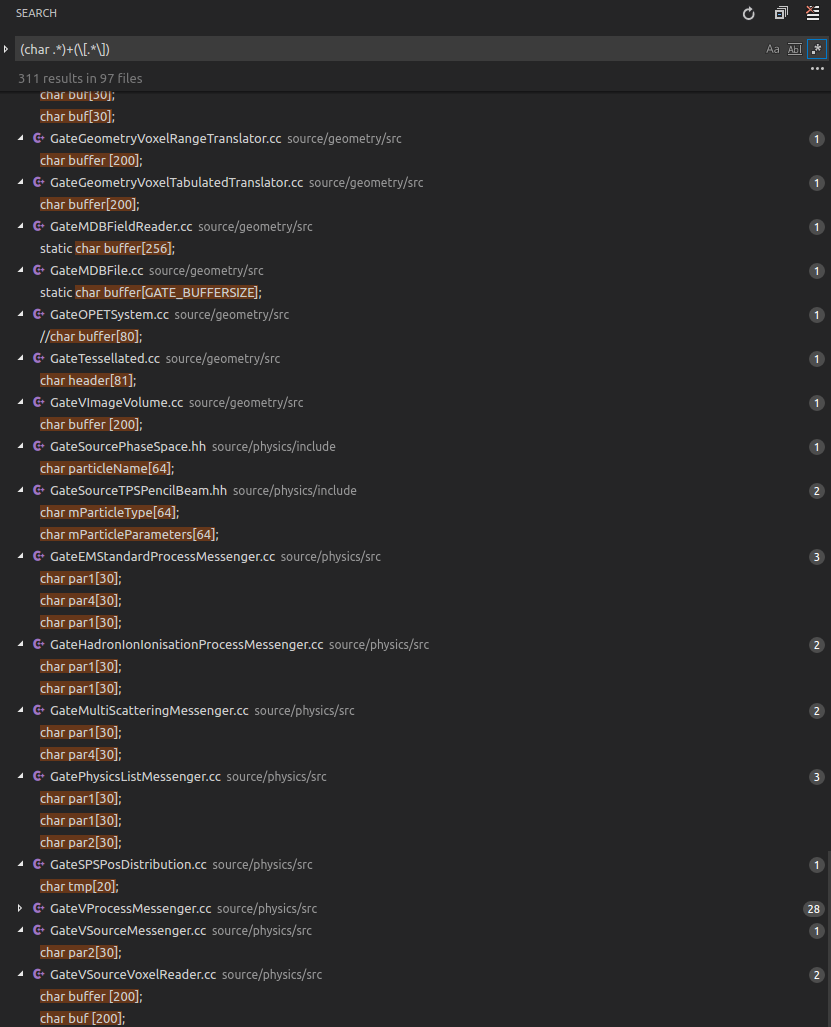
From Googling around I learned that "stack smashing" usually happens with static arrays, like char buffer[200];. If I understood correctly, this actually only happens with gcc because gcc inserts "canaries" to detect buffer overflows, and upon detection it throws theses "smashing" exceptions. With other compilers (or with the canaries disabled in gcc) you'd just get segmentation faults or undefined behavior.
There are quite a lot of static arrays used in the Gate source code. I have not yet hunted down which of them might be responsible for the above crash case, but in general I think it's a bad programming style and I think it would be good if most of them would be replaced with safer solutions.
You are right, static size arrays is not a good habit (even if it is useful sometimes), but hunting them down could be tedious ... We can keep in mind to replace some of them when we meet in the code. thanks
Occurences